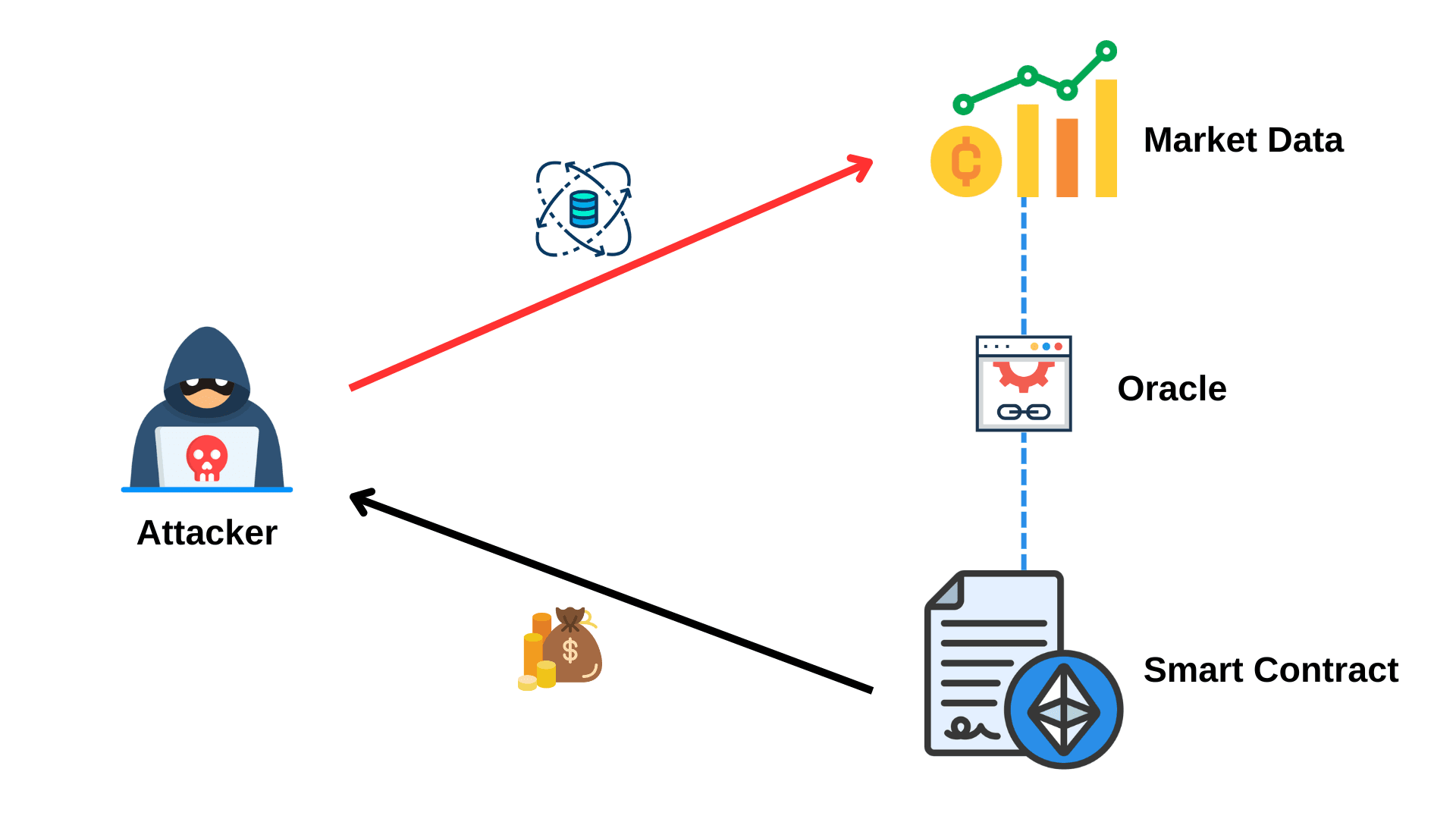
Introduction
In the rapidly evolving financial ecosystem, blockchain technology—particularly smart contracts—has emerged as a transformative force, enabling trust, transparency, and automation in ways previously unimaginable. These self-executing contracts have the potential to address many of the inefficiencies and challenges present in traditional systems by removing intermediaries, ensuring immutable record-keeping, and streamlining operations. However, the capabilities of smart contracts are inherently limited when they rely exclusively on on-chain data.
Without access to external information, their functionality remains constrained to predefined rules and blockchain-native interactions. To unlock their full potential, smart contracts require secure, reliable, and tamper-proof connections to off-chain data sources, enabling them to perform more complex and meaningful tasks.
This is where oracles play a pivotal role. Oracles act as a critical bridge between the deterministic environment of blockchains and the dynamic, unpredictable nature of the real world. They provide the data pipelines necessary for smart contracts to access external inputs such as market prices, weather conditions, event outcomes, or even IoT device readings.
By facilitating this secure communication, oracles empower smart contracts to automate and execute actions based on real-world events, thereby expanding their use cases across industries like finance, supply chain, insurance, and beyond. In essence, oracles are the cornerstone of making smart contracts truly "smart," enabling them to operate as dynamic, versatile tools for solving real-world problems in a decentralized and trustless manner.
What is an Oracle?
As previously highlighted, oracle is critical in bridging the gap between smart contracts and real-world data. Oracles serve as a secure solution for integrating off-chain data into on-chain environments. By facilitating access to external data sources, oracles significantly enhance the functionality of smart contracts, overcoming the limitations associated with relying exclusively on on-chain data.
Oracle can bring invariant types of data, For example, lending platforms like Aave and Compound rely on oracles to determine the collateralization levels of loans. One type of data frequently used in financial systems is price data. A price oracle is responsible for bringing market prices onto the blockchain. However, if it’s not developed cautiously, this process can expose the smart contract to a vulnerability known as price oracle manipulation.
How Does Price Oracle Manipulation Work?
1. Low Liquidity Assets
Assets with low liquidity on decentralized exchanges are easier targets for attacks because their prices can be influenced more easily, allowing attackers to manipulate oracles that rely on these prices.
2. Flash Loan Attacks
A flash loan is a method of borrowing assets without collateral and repaying them within the same transaction. This strategy can be used in an attack by borrowing a significant amount of cryptocurrency, executing trades on a decentralized exchange (DEX), manipulating the price, and affecting smart contract calculations, then repaying the borrowed funds after exploiting the oracle.
3. Data Source Exploitation
Manipulating market prices through high-volume trades or using flash loans is not the only method attackers can use for this type of attack. Another approach is exploiting the data source itself. In this scenario, the actual market price may remain stable and accurate, but the attacker targets the data source that reports price data to the oracle. Therefore, oracles relying on a single data source are more vulnerable compared to those aggregating data from multiple sources.
4. Cross-Protocol Manipulation
By exploiting interconnected DeFi protocols, attackers can manipulate oracles in one protocol to indirectly affect another. For example, manipulating the price of an asset in a DEX could alter the collateralization status in a lending protocol.
5. Time Bandit Attacks
Miners or validators with significant power might reorder transactions in a block to exploit oracle updates. This is particularly relevant in proof-of-stake or proof-of-work systems with low validator diversity.
6. Sybil Attack
A Sybil attack in the context of price oracle manipulation occurs when an attacker creates multiple fake or fraudulent identities (nodes) within a decentralized oracle network to gain undue influence over the price data being aggregated and delivered to smart contracts. By dominating the network, the attacker can manipulate the price data in their favor, potentially causing significant financial damage to blockchain applications relying on that data.
The protections
1. Use multiple Oracles
Using multiple oracles can reduce the risk of attacks because an attacker cannot manipulate the oracle output by gaining access to a single source.
2. Time-Weighted Average Prices (TWAP)
The advantage of using TWAP (Time-Weighted Average Price) is that it calculates the average price over a specific period of time. This approach reduces the impact of sudden price changes, as the price is averaged out over the selected timeframe.Often Flashloan attacks borrow huge sums, but return all the funds within a single transaction, resulting in temporary price peaks for the protocol. Using a TWAP would reduce the impact of this single price peak. Even more secure is to cut off extreme value from the price calculation.
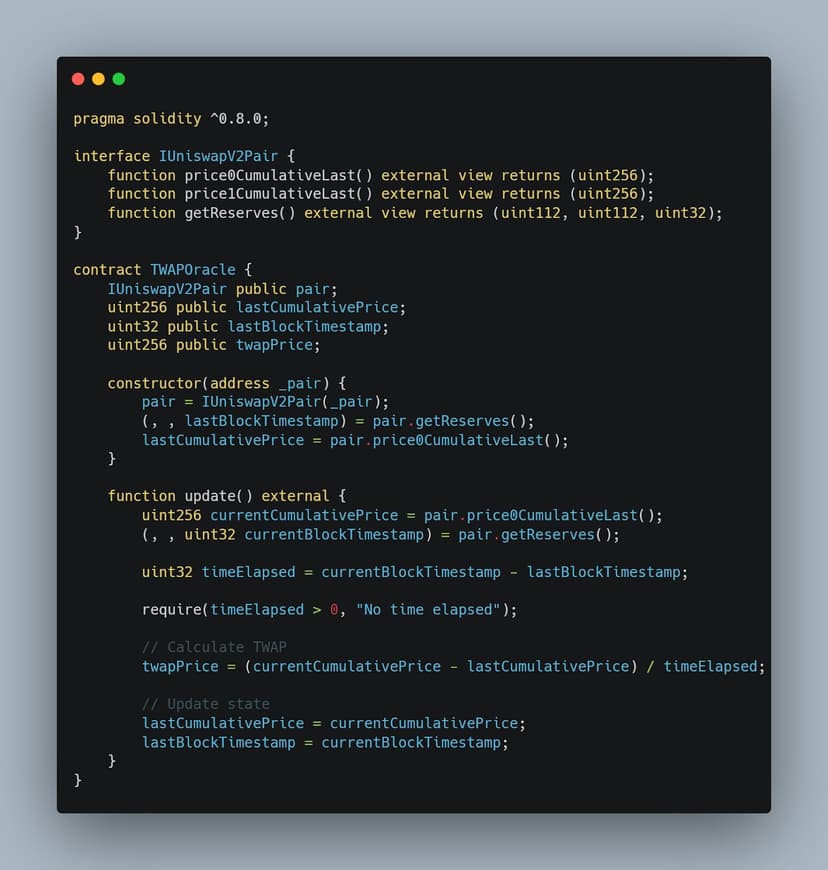 Example Code
Example CodeIn the example smart contract, you can see that it relies on a single-source oracle for data from the DEX, which can be vulnerable. However, by using a time-weighted average price, this vulnerability can be mitigated.
3. Decentralized Oracle Networks (DONs)
Data from a decentralized network of nodes is ideal and more reliable than relying on a single data source. Nodes are entities responsible for fetching and verifying external (off-chain) data and delivering it to smart contracts on the blockchain.
This approach distributes trusted data across multiple nodes, aligning with the core concept of blockchain technology. This is similar to 1 but not the same, what is the role of nodes in an oracle price manipulation and how does it happen?
4. Increase Liquidity in Key Pools
Ensuring that liquidity pools used by oracles are sufficiently deep can mitigate the price impact of large trades.
5. Onchain Monitoring
Continuously monitor transactions and flag anomalous activities, such as unusually large trades or rapid price changes.
6. Rate Limiting and Circuit Breakers
Set thresholds for price deviations. If a price change exceeds a certain limit within a short time, the protocol can temporarily halt operations to investigate.
7. Redundancy in Oracle Providers
Relying on multiple oracles ensures that a single point of failure does not compromise the protocol. If one oracle reports an anomaly, others can validate its accuracy.
8. Incentivized Whistleblowing:
Encourage community members to report potential vulnerabilities or suspicious activities by offering rewards.
Conclusion
An oracle is a crucial component of smart contract development, enabling access to off-chain data for Web3 products. However, improper implementation can turn it into a vulnerability that attackers might exploit to manipulate smart contracts. Therefore, careful design and the use of secure methods and protocols are essential.
Want to read more?
https://moodglobalservices.com/blog/understanding-the-risks-of-sharing-control-in-smart-contracts-delegatecall-vulnerability
https://moodglobalservices.com/blog/account-abstraction-in-simple
Sources:
https://medium.com/@DeCommas/oracles-in-web3-api-development-28b8dd3c13f1
https://www.halborn.com/blog/post/what-is-oracle-manipulation-a-comprehensive-guide
https://chain.link/education-hub/market-manipulation-vs-oracle-exploits